Zero Trust security strategy, when boiled down to one message becomes, “Never trust, always verify”. More specifically, Zero Trust instructs that implicit trust should not be granted to any user, device, or application without verification.
Zero trust is an essential change in thinking from the more traditional perimeter security strategy where attacks were mainly perceived to be from outside of the organisation. However, the consensus now is that a wall (e.g. a collection of firewalls) to keep out the outside world and total trust of everyone inside its perimeter is also unsafe. Under a perimeter security approach, a cyber attacker only needs to hack one employee’s credentials and then they can move laterally through the entire system. Perimeter security is now particularly insufficient, due to the increase in adoption of cloud services, employees working from home, and the surge in the number of personal devices used since the model was popularised. The perimeter has become simply unmanageable, and often unidentifiable.
Network locality is not sufficient for deciding trust in a network.”
Gartner, 2020
Zero Trust is the realisation and resultant security strategy that implicit trust of anyone or anything is a risk that no organisation can afford to take. The US government has taken advice and determined that by 2024 all ‘networks’ will be subject to Zero Trust compliance.
What is Zero Trust?
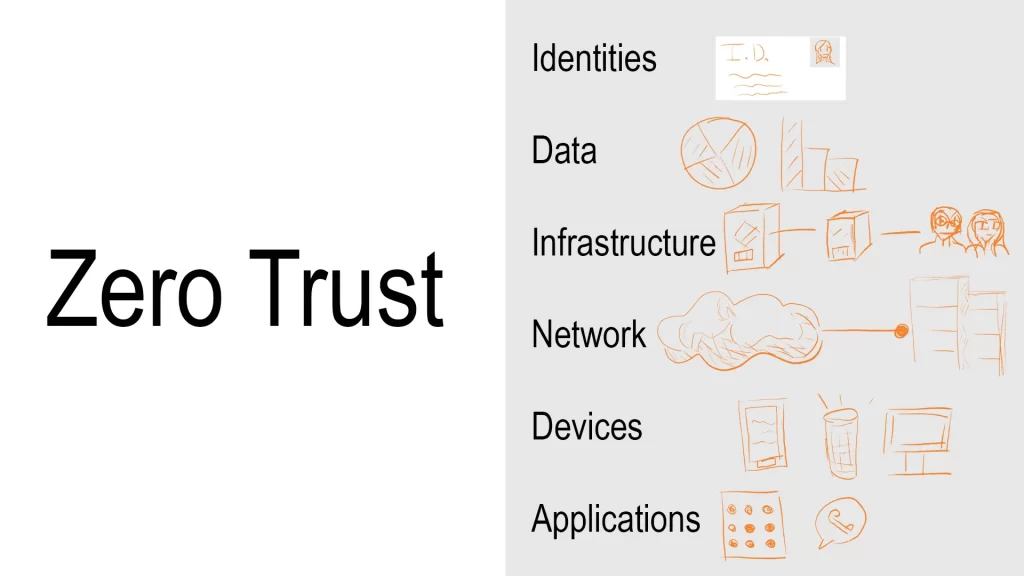
IBM defined three core principles within a Zero Trust Strategy:
1. “Never trust, always verify.”
New connection attempts should be verified and authorised and not automatically trusted due to their location or who they claim to be.
2. “Implement least privilege.”
Reconsider your infrastructure. Users and applications should be granted the minimum amount of access necessary to perform their jobs.
3. “Assume Breach.”
Plan and manage the risks associated with cyberattacks, and minimise the ‘impact zones’ of such breaches. Do this from as many data sources as possible.
Why ‘Trust’?
Trust is an essential part of our human nature, unfortunately, this has made past security strategies deeply flawed. It’s reassuring to think that the people we see every day have only good intentions, but that is an assumption: that they are who we assume them to be. Even if they are not a hacker in disguise or a corporate spy, what in your organisation is stopping a disgruntled, or recently fired employee from stealing vast amounts of data?
Zero Trust does not mean penalising employees or turning a cold shoulder. It means minimising the risk. Devising a strategy where if any one user ‘went rogue’ on your system, they could only do the least amount of damage.
Zero Trust and the National Institute of Standards and Technology (NIST) Guidelines
Zero trust can consist of monitoring all network communications, avoiding default configurations, tracking all devices, and implementing multifactor authentication.”
Luke Irwin, NIST, 2019, https://www.itgovernanceusa.com/blog/implementing-zero-trust-with-iso-27001
In more detail, a Zero Trust strategy works well with further guidelines from the National Institute of Standards and Technology:
1. Repeated verification
A login and verification process only gives your organisation sufficient protection if it’s done frequently. Signing in once at the start of the week and relying on a device to store your credentials with no verification checks is a one-way ticket to your account being breached.
2. Limit the “breach scope”
Scrutinise what data each employee needs access to for their role.
3. Automate prevention, detection, and response
At Differentia Consulting we a passionate about Hyper Automation, and so we would advise you not just to automate the prevention, detection, and response but to Hyper Automate them. Contact us: [email protected] to learn how.
Zero Trust is Integral to Governance Risk and Compliance
Zero Trust will become the norm as part of your cyber security strategy and CyberHygiene considerations when reviewing vendor-risk-management policies and procedures.

Start your Active Intelligence journey today.
Differentia Consulting provides #SmarterBI solutions offering full life cycle services and complementary business discovery solutions.
Call us on +44 1494 622 600 or email: [email protected]






